Introduction to Cryptography – C839 memorize this to share PDF
| Title | Introduction to Cryptography – C839 memorize this to share |
|---|---|
| Author | Allen Hope |
| Course | Introduction to Cryptography |
| Institution | Western Governors University |
| Pages | 7 |
| File Size | 160.4 KB |
| File Type | |
| Total Downloads | 441 |
| Total Views | 500 |
Summary
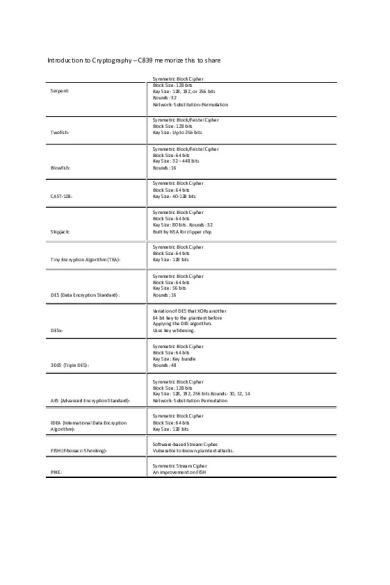
Introduction to Cryptography – C839 memorize this to shareSerpent:Symmetric Block Cipher Block Size: 128 bits Key Size: 128, 192, or 256 bits Rounds: 32 Network: Substitution-PermutationTwofish:Symmetric Block/Feistel Cipher Block Size: 128 bits Key Size: Up to 256 bitsBlowfish:Symmetric Block/Feist...
Description
Introduction to Cryptography – C839 memorize this to share
Serpent:
Symmetric Block Cipher Block Size: 128 bits Key Size: 128, 192, or 256 bits Rounds: 32 Network: Substitution-Permutation
Twofish:
Symmetric Block/Feistel Cipher Block Size: 128 bits Key Size: Up to 256 bits
Blowfish:
Symmetric Block/Feistel Cipher Block Size: 64 bits Key Size: 32 – 448 bits Rounds: 16
CAST-128:
Symmetric Block Cipher Block Size: 64 bits Key Size: 40-128 bits
Skipjack:
Symmetric Block Cipher Block Size: 64 bits Key Size: 80 bits. Rounds: 32 Built by NSA for clipper chip
Tiny Encryption Algorithm (TEA):
Symmetric Block Cipher Block Size: 64 bits Key Size: 128 bits
DES (Data Encryption Standard):
Symmetric Block Cipher Block Size: 64 bits Key Size: 56 bits Rounds: 16
DESx:
Variation of DES that XORs another 64 bit key to the plaintext before Applying the DES algorithm. Uses key whitening.
3DES (Triple DES):
Symmetric Block Cipher Block Size: 64 bits Key Size: Key bundle Rounds: 48
AES (Advanced Encryption Standard):
Symmetric Block Cipher Block Size: 128 bits Key Size: 128, 192, 256 bits Rounds: 10, 12, 14 Network: Substitution Permutation
IDEA (International Data Encryption Algorithm):
Symmetric Block Cipher Block Size: 64 bits Key Size: 128 bits
FISH (Fibonacci Shrinking):
Software-based Stream Cipher. Vulnerable to known plaintext attacks.
PIKE:
Symmetric Stream Cipher An improvement on FISH
RC4:
Symmetric Stream Cipher Used identically for encryption and decryption as the data stream is simply XORed with the key. Uses variable length key from 1 to 256 bytes. Generates pseudo-random strings of bits.
RC5 and RC6:
Symmetric Block Mode Ciphers Key Size: Variable up to 2048
Elliptic Curve Cryptography (ECC):
Asymmetric. Key Size: Variable up to 160 bits. Generates key pairs based on a mapped curve. Endorsed by NSA. Size of curve determines difficulty Of finding the algorithm.
ElGamal:
Asymmetric Encryption Algorithm. Based on Diffie-Hellman. Used in some PGP and GPG software.
Diffie-Hellman:
First publicly described asymmetric Algorithm. Cryptographic protocol that allows two parties to establish A shared key over an insecure channel.
RSA (Rivest, Shamir, Aldeman):
Based on difficulty of factoring Product of two large prime numbers. Key Size: 1024 – 4096 bits. Most widely used public key cryptography Algorithm in existence.
Menezes-Qu-Vanstone (MQV):
Protocol for key agreement. Based On Diffie-Hellman
MD5 (Message Digest 5):
Hash Size: 128 bits Block Processing: 512 bits
SHA-1:
160 bit hash function similar to MD5. Designed by NSA.
SHA-3:
Developed by NIST in 2015. Bitrate.
FORK-256:
512 bit blocks. Each block hashed into 256 bit blocks in parallel. Under review, not widespread.
RIPEMD-160 (RACE Integrity)
Primitives Evaluation Message Digest): 128, 256, 320 bit versions. More secure than MD5.
GOST:
Russian hash algorithm. Hash Size: 256 bits.
Digital Signature Algorithm (DSA):
Requires prime numbers and modulus Operations. Adopted by the US in 1993
Electronic Code Book (ECB):
Blocks encrypted independently, But identical plaintext blocks = Identical ciphertext blocks IV used on first block. Most basic encryption mode.
Cipher Block Chaining (CBC):
Each block of plaintext XORed With previous ciphertext block Before being encrypted. Produces more randomness, which Is more secure.
Propagating Cipher Block Chaining (PCBC):
Each plaintext block XORed with the XOR Of previous plaintext block and previous Ciphertext block before being encrypted.
Cipher Feedback (CFB):
Allows encryption of partial blocks.
Output Feedback (OFB):
Generates keystream blocks that Are XORed with the plaintext blocks. Turns block cipher to stream cipher.
Counter (CTR):
Turns block cipher to stream cipher Like OFB. Generates next keystream block by Encrypting successive values of a counter.
Stream Ciphers:
RC4, FISH, PIKE
Key Clustering:
Different encryption keys generate same ciphertext from the same plaintexts.
Symmetric Encryption Equation:
C = E(k,). C=Ciphertext, E=Encryption Function, K=key, P=plaintext.
Symmetric Decryption Equation:
P=D(k,c). P=Plaintext. D=Decryption Function, K=key, C=ciphertext.
Keyspace:
Refers to the number of possible keys. Calculated by 2^ key size in bits.
Whitening:
XORing in an additional key.
Feistel Function:
Basis for most block ciphers. Splits blocks of plaintext data (often 64 bits) into two parts, L0/R0
Symmetric Stream Ciphers:
Sometimes called state ciphers. Stream of pseudo-random digits Is generated independently and Is combined with plaintext to Encrypt or ciphertext to decrypt
Type 1 Algorithms:
Used for classified or sensitive information.
Type 2 Algorithms:
Used for unclassified equipment, assemblies, or components. Skipjack and KEA.
Type 3 Algorithms:
Device for use with sensitive but unclassified (SBU) on non-national security systems. DES, 3DES, SHA, AES.
Type 4 Algorithms:
Registered by NIST but not FIPS published. Unevaluated commercial cryptographic equipment that neither NSA nor NIST certify for government use.
Authentication Protocols:
Password Authentication Protocol (PAP): Username/Password over HTTP sent In cleartext-main weakness. Most basic form of authentication. Passwords stored in table are encrypted, transmissions aren’t. HTTP uses for authentication.
Shiva Password Authentication Protocol (SPAP):
Challenge Handshake Authentication Protocol (CHAP):
Like PAP but sent over encrypted channels. Proprietary version of PAP. Encrypts username and password during transmission. Shares a hash with the client system. Challenge is sent with acknowledgement, Otherwise connection is terminated. After link establishment, authenticator sends challenge message to peer, peer responds with one-way hash function. Authenticator checks response against its own calculation. New challenge at random intervals.
Ciphers: Mono-Alphabet Substitutions:
Includes Caesar, Atbash, Affine, ROT 13
Caesar Cipher:
Shift letters a certain number of times. Most common is shift of 3
Atbash Cipher:
Substitutes A for Z, B for Y, etc.
Affine Cipher:
Letter is mapped to some numeric Value, permuted with simple math Function, then converted back to A letter. Ax + b (mod M)
Null Cipher:
Hidden message in unrelated text
Book Cipher:
Agree on a book, send coordinates for words
Rail Fence Cipher:
Transposition cipher. Plaintext written In columns/transposed in rows.
Multi-Alphabet Substitution:
Rotates through multiple various Alphabets, such as +1, -1, +2
Multi-Alphabet Substitutions:
Cipher Disk Vigenere Cipher Enigma Machine
Cipher Disk:
Physical device (disk) that was turned To encrypt. Poly-Alphabetic, each turn used a new cipher.
Vigenere Cipher:
Poly-Alphabet cipher that used a series Of different mono-alphabet ciphers Based on the letters of a keyword. Effective prior to advent of computers.
Enigma Machine:
Electromechanical rotor-based cipher Used by Germans in WWII
Playfair Cipher:
Encrypts two letters rather than one. Uses a 5 x 5 table.
ADFGX Cipher:
Transposition cipher used by the German Army in WWI which used a modified Polybius square with a single columnar Transposition used to encode a 36-letter Alphabet. Key is 6 x 6 table
Homophonic Substitution:
Earlier attempt to make substitution Ciphers more robust by masking Letter frequencies. Plaintext letters Map to more than one ciphertext symbol.
Scytale:
Physical cylinder tool used by Greeks To encrypt messages.
Kasiski Examination:
Method to deduce length of keyword used in a polyalphabetic substitution cipher. Once length of the key is known you line up the ciphertext in columns. Each column can be treated as a mono-alphabet substitution.
Chosen Plaintext Attack:
Attacker obtains ciphertexts corresponding to set of plaintexts of his choosing. Allows attacker to attempt to derive the key.
Ciphertext Only Attack:
Attacker only has a collection of ciphertexts. Completely successful if corresponding plaintexts or key can be deduced. Result is often a partial break.
Related-Key Attack:
Attacker obtains ciphertexts encrypted under two different keys. Requires that both keys be closely related.
Linear Cryptanalysis:
Commonly used on block ciphers. Known plaintext attack that uses linear approximation to describe behavior of block cipher. Bits of info about key can be obtained from enough pairs of plaintext/ciphertext.
Differential Cryptanalysis:
Applicable to symmetric key algorithms. Examines differences in input and how it affects output. Worked only with chosen plaintext, but could also work with known plaintext and ciphertext.
Integral Cryptanalysis:
Useful against block ciphers. Based on substitution/permutation networks as an extension of differential cryptanalysis. Looks at pairs of inputs that differ in only one bit.
Cryptanalysis Resources:
Time, Data, Memory
Instance (local) Deduction:
Attacker discovers additional plaintexts or ciphertexts not previously known.
Information Deduction:
Attacker gains some Shannon info about plaintexts or ciphertexts not previously known.
Types of Random Number Generators:
Table Look Up, Hardware, Software
Fortuna:
Group o PRNGs. Uses a seed file.
Lagged Fibonacci Generator (LFG):
Sequence of numbers by adding Previous two numbers to create The next. Can be added, multiplied, or XORed.
Blum Blum Shub:
Very effective PRNG. Difficult to Predict the outcome because of the Quadratic residuosity problem
Public Key Infrastructure (PKI):
Contains certs and public keys. Users identified via CA. Contains CRL And new method Online Certificate Status Protocol (OCSP). Uses Asymmetric key pairs and combines software, encryption, and services to provide a means of protecting security of business communication/transactions.
Public Key Cryptography Standards (PKCS):
In place by RSA to ensure uniform certificate management throughout the internet.
Registration Authority (RA):
Takes burden off of CA by handling verification prior to certificates being issued. Acts as proxy between user and CA. Receives requests, authenticates, forwards to the CA.
Certificate Policy:
Set of rules that defines how a certificate may be used.
Certificate Authority (CA):
Primary role is to digitally sign and publish public key bound to a given user. Entity trusted by one or more users to manage certificates. Godaddy and Verisign.
Phases of Key Lifecycle:
Setup and initialization phase. Administration phase. Cancellation phase.
Trust Models:
Hierarchical Single Authority Web of Trust
Online Certificate Status Protocol (OCSP): Certificate Revocation List (CRL):
Real-time protocol for verifying certificates. List of certificates issued by CA that are no longer valid. Push Model: CA automatically sends CRL out. Pull Model: CRL is downloaded from CA by end user.
X.509 Certificates:
Relied on by S/MIME, issued by Cas, used to digitally sign information. V3 most common
X.509 Certificate Content:
Version, holder’s public key, serial number, holder’s distinguished name, validity period, name of issuer, digital signature of issuer, signature algorithm identifier.
Wired Equivalent Privacy (WEP):
Uses RC4 stream cipher. 40 bit key With 24 bit IV to combine a 64 bit Encryption. 128 bit WEP uses 104 bit w/ 24 bit IV. Same traffic key must never be used twice. 50% chance every 5000 packets to use same key. Transmits IV in plaintext.
Digital Signatures:
Not for confidentiality. Used to guarantee who sent the message. Reverses asymmetric encryption, sender encrypts with their private key. Usually the encryption of a message or message digest with the sender’s private key. To verify signature, recipient uses sender’s public key.
Digital Signatures Provide:
Authentication, Integrity, Non-repudiation
Diffusion:
Having changes to one character in the Plaintext affect multiple characters in The ciphertext.
Confusion:
Attempts to make relationship between Statistical frequencies of the ciphertext And actual key as complex as possible. Occurs by using complex substitution Algorithm.
Avalanche:
A small change yields large effects In the output.
Natural Numbers (N):
Sometimes called the counting Numbers. (1, 2, 3)
Integers (Z):
Whole numbers (-1,0,1,2). Natural Numbers plus negatives and zero.
Rational Numbers (Q):
Ratios of integers (3/2, 17/4, 1/5)
Real Numbers (R):
Includes rational numbers and numbers That cannot be expressed as a ratio of Two integers such as square roots
Imaginary Numbers (I):
Numbers whose square is negative
Entropy:
Measure of the uncertainty associated With a random variable.
Pretty Good Privacy (PGP):
Not an algorithm itself, uses other asymmetric/symmetric algorithms. Most often associated with email encryption. Can also be used to create certificates.
Wi-Fi Protected Access (WPA):
Uses TKIP, which is a 128 bit per-packet key. Dynamically generates a new key for each packet.
WPA Modes:
Personal: Also referred to as WPA-PSK mode. Designed for home/small networks. Each device authenticates with the AP using the same 256 bit key. Enterprise: Also referred to as WPA-802.1x mode. Designed for enterprise networks, requires a RADIUS server for authentication. EAP is authentication protocol.
WPA2:
Based on IEEE 802.11i standard. Uses AES and CCMP. Provides data confidentiality, authentication, and data integrity.
SSL Process:
Browser asks web server to prove identity. Server replies with copy of its SSL certificate. Browser checks to see if certificate is from a CA it trusts. Server sends back digitally signed acknowledgement and session is started.
TLS Handshake Process:
Client connects to server requesting secure connection and presents a list of encryption/hash functions it can support. Server picks strongest encryption/hash function and notifies client of the chosen algorithms. Server sends back its digital certificate (X.509). Client encrypts random number with the server’s public key and sends result to server. Server decrypts with its private key. From the random number both parties generate key material for encryption and decryption.
Point-to-Point Tunneling Protocol (PPTP):
Used to secure point to point protocol (PPP), encrypts packets with Microsoft point to point encryption and authenticates users with EAP or CHAP. Works at the data link layer. Only works on standard networks.
Layer 2 Tunneling Protocol (L2TP):
Enhancement to PPTP, works at the data link layer of the OSI model, offers 5 methods of authentication, works on X.25 and ATM networks as well as standard IP networks. Uses IPSec for encryption.
Internet Protocol Security (IPSec):
Encrypts the packet and the header information. Has protection against unauthorized retransmission of packets.
SSL/TLS VPN:
VPN is set up through a web browser. User logs into a web portal, via their browser. Gives the user access to the target network.
Encrypting File System (EFS):
Implemented by Microsoft since Windows 2000 as part of NTFS file system. Way to encrypt and decrypt files and folders. Right-click, properties, advanced....
Similar Free PDFs

Things to memorize
- 1 Pages

Formulas to memorize exam 2
- 1 Pages

Introduction to
- 22 Pages

Introduction to Ninth Edition Introduction to
- 1,073 Pages

Study Guide for Content to Memorize
- 39 Pages

Full immuno notes to share
- 87 Pages

Introduction to Cakes Homework
- 42 Pages
Popular Institutions
- Tinajero National High School - Annex
- Politeknik Caltex Riau
- Yokohama City University
- SGT University
- University of Al-Qadisiyah
- Divine Word College of Vigan
- Techniek College Rotterdam
- Universidade de Santiago
- Universiti Teknologi MARA Cawangan Johor Kampus Pasir Gudang
- Poltekkes Kemenkes Yogyakarta
- Baguio City National High School
- Colegio san marcos
- preparatoria uno
- Centro de Bachillerato Tecnológico Industrial y de Servicios No. 107
- Dalian Maritime University
- Quang Trung Secondary School
- Colegio Tecnológico en Informática
- Corporación Regional de Educación Superior
- Grupo CEDVA
- Dar Al Uloom University
- Centro de Estudios Preuniversitarios de la Universidad Nacional de Ingeniería
- 上智大学
- Aakash International School, Nuna Majara
- San Felipe Neri Catholic School
- Kang Chiao International School - New Taipei City
- Misamis Occidental National High School
- Institución Educativa Escuela Normal Juan Ladrilleros
- Kolehiyo ng Pantukan
- Batanes State College
- Instituto Continental
- Sekolah Menengah Kejuruan Kesehatan Kaltara (Tarakan)
- Colegio de La Inmaculada Concepcion - Cebu








