Acquisition of Digital Forensics Evidence PDF

| Title | Acquisition of Digital Forensics Evidence |
|---|---|
| Author | Melisa Davis |
| Course | Digital Forensics |
| Institution | Liberty University |
| Pages | 5 |
| File Size | 162.3 KB |
| File Type | |
| Total Downloads | 84 |
| Total Views | 146 |
Summary
Acquisition of Digital Forensics Evidence Assignment...
Description
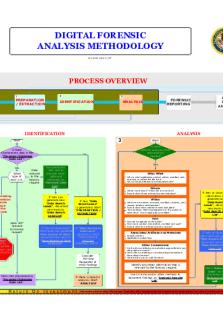
UNIT 3: ACQUIRING DIGITAL FORENSICS EVIDENCE Overview In the previous lesson, you learned more about the importance of Computer Forensics as well as its history and background information. You also explored more details about the skills, education level, and training required to become a computer forensic investigator as well as various job opportunities available for you in the field of computer forensics. In this unit, you will learn about acquiring digital forensics evidence, which include the proper ways to acquire, handle, and analyze digital evidence. You will explore essential techniques used to investigate offenses, such as the Image Method for investigating financial frauds, and diagnosing hardware networks for forensics evidence. Now that you understand that computers are used to commit various felonies, you need to know how you can acquire digital forensics evidence as a Digital Forensics Investigator. Digital forensics typically involves a sequential process which include: 1. Seizing the media; 2. Acquisition of the media- creating an image of the media for forensics examination; 3. Analysis of the Forensics Image; and 4. Reporting (Novak, Grier & Gonzales, 2019).
SEIZURE
ACQUISITION
ANALYSIS
REPORTING
Figure 1: General Phases of Digital Forensics
Evidence Acquisition Before acquiring the evidence, the investigator should first locate it. Digital evidence is typically found in hard drives, but with the current advancement in computing technology, evidence can be located in almost all digital-aware gadgets (Hassan, 2019). According to Hassan (2019), some of the devices that can be investigated for forensics evidence include Laptops, Desktops, Tablets, Servers and RAIDs, Network Devices like routers, modems, switches, and wireless access point, IoT devices and Internetenabled devices used in home automation. Digital forensic investigators typically maintain a proper chain of custody. The primary goal of maintaining excellent handling in the acquisition process is to ensure evidence integrity and prevent tampering with evidence. The chain should be answers to: Who collected it? How and where? Who took possession of it? How was it stored and protected in storage? Who took it out of storage and why? The fundamental principle when it comes to acquisition is that Digital Forensics Evidence is “fragile” and individuals can alter, destroy, or damage it through inappropriate examination or handling. Therefore, Digital Forensics Investigators should take special precautions in preserving forensic evidence, primarily because failure to do it can result in it being unusable or contribute to the incorrect
conclusion (Ashcroft, Daniels & Hart, 2019). According to the National Institute of Justice, the original Digital Forensics Evidence should be acquired in a way that preserves and protect the evidence. The following are some of the fundamental steps in obtaining evidence: Securing the digital evidence based on the departmental guidelines Documenting the software and hardware configuration of the examiner’s system Verifying operation of the forensics investigator’s computer system to include software and hardware Disassembling the computer’s case to be assessed or investigated to allow physical access to its storage drives or devices. In this step, the Digital Forensics Investigator should ensure that the equipment is protected from any magnetic fields and electric fields. Identifying the computer’s storage device that should be acquired, which can either be internal or external or both.
Analysis In the Forensics Analysis Phase, the image and contents available from the images of the acquired devices and its files are examined using different forensic tools. The primary goal in this phase is to search for any available leads within the acquired copy/duplicate. Digital Forensics Investigators use specialized tools such as Sleuth Kit, Encase, Forensic Toolkit (FTK), among others (Nikkel, 2016) to recover and retrieve deleted, hidden, and encrypted files as well as the IM chat logs, deleted e-mails, and Internet browsing history (Hassan, 2019). Investigators’ forensics tools apply the hash signature analysis to detect and identify essential files in the image content and exclude familiar files. Hassan (2019) argue that hashed contents of the acquired image files are compared to the lists, which have been prepared and compiled, like the Reference Data Set (RDS) from the National Software Reference Library. The critical purpose of this step is to get the software from multiple sources, where the examiner incorporates the file profiles analyzed and computed from the software into the RDS of information (Hassan, 2019). Forensics investigators then use the RDS to review files on the acquired device, mainly by matching those file profiles in RDS.
Image Method for Investigating Financial Frauds Digital forensics analysis can also be used in tracking down hidden assets obtained as a result of financial fraud. Any computing device such as personal laptops, work computers, tablets, or phones involved in conducting the financial fraud or any other activity leave a crucial trail of digital forensics evidence. Image technique is applied to uncover such scams. In this case, forensics investigators use forensic tools like ProDiscover, EnCase and FTK to connect to the targeted or suspected computer system responsible for the financial frauds (Kent, Chevalier, Grance & Dang, 2006). Investigators may either use hardware or software tools to obtain digital evidence using the image method. In the acquisition phase, the investigator typically deals with secondary storage devices in computing. These devices include Solid State Drive (SSD), thumb drive, and Hard Disk Drive (HDD). According to Hassan (2019), if the computer was still running, another secondary storage assessed is the volatile memory (RAM). The Digital Forensics Investigator is supposed to conduct a duplication or create a complete image of the suspected hard drive, a process called bit-to-bit model (Hassan, 2019). Consequently, an analysis is conducted on the digital copy or image created later. Investigators typically use software imaging or hardware duplicators tools such as the DD command for computers using Linux OS to produce a duplicate drive. When performing the imaging process, Digital Forensics Investigators are supposed to remember that the suspected hard drive need to be write-protected, primarily to protect and prevent the original disk
from being damaged or tempering with the initial evidence (Ashcroft, Daniels & Hart, 2019). If the computer under investigation is still running, volatile memory (RAM) should also be acquired. When it comes to evidence acquisition, Digital Forensics Investigators need to produce several images or copies of the acquired drive. Forensics analysis is only conducted on the created images of digital evidence, and therefore, the original media, computer, or drive should remain intact. The image acquired using the hardware tools are categorized into two primary parts, that is, bridges and embedded (Akbal & Dogam, 2018). Investigators can take the forensic image directly through the hardware tool, primarily using an embedded device. According to Akbal & Dogam (2018), forensic images of judicial devices lined to the connection interface of that hardware is created through configurations made from the interface of a web or those on the connected hardware. The imaging method used to investigate various financial frauds focus on several areas such as the e-mail contents, spreadsheets and other files, accounting or budgeting software programs, Internet browsing history, metadata analysis, mobile phones, among other activities (RSM., 2018). Forensic Investigators obtain an image of electronic devices with potential evidence of financial frauds such as mobile devices and computer hard drive, which is analyzed without using the original media seized. All files and fraudulent transactions information is extracted, even the deleted, encrypted, protected, iterated, and duplicated files. These items, information, and data obtained from the image can be used to provide essential details towards indicating potential financial fraud.
Diagnosing Hardware Networks Forensics Investigators may consider network diagnostic and troubleshooting hardware for capturing forensic evidence. Almost every computing device is connected to the network, and they are internetenabled. Network forensics is the process of obtaining, recording, and analyzing suspected network packets to find out potential sources of network security attacks (INFOSEC., 2019). According to Infosec (2019), network forensics investigators focus on analyzing network traffic information and data when it comes to the acquisition of evidence. Evidence is gathered from various webs and network tools like IDS and Firewalls. Similarly, many scholars recommend debuggers when it comes to diagnosing distributed systems. Debuggers can be used by the forensic investigators to acquire digital forensics evidence, given the fact that they are capable of producing “backtrace” to assist the examiner in understanding what occurred in distributed systems (Prosise & Mandia, 2016; Handigol et al., 2016). According to Handigol et al. (2016), in SDNs, forensic experts may use Net-sight and ndb systems to produce “packet histories,” which can be used as forensic evidence. When packets traverse SDN switches, the network switches typically assembles “postcards” regarding the packets, which is sent to the centralized NetSight servers. NetSight servers, after receiving the packets, answers the diagnostic questions on what occurred to a specific packet (Nikkel, 2016). It is an alternative method to acquire forensic evidence, where the investigator bypasses the standard USB, SATA, or SAS interfaces, and access the suspected storage media or hardware using the diagnostic or debug ports that are built into the devices’ drive (Nikkel, 2016). Forensics investigators connect the serial port access to the disk firmware and power the drive on, a dialogue box with boot message appears. Investigators enter CTRL-Z to put the hardware drive in a diagnostic mode, primarily using a command prompt provided by the drive firmware/hardware (Nikkel, 2016). Forensic investigators, from the diagnostic interface provided, can retrieve and collect detailed underlying information regarding the drive. Diagnosing hardware network displays diagnostic interfaces to the forensic examiners, which give them access to the drive sectors in the areas of the specific system as well as other critical information that is not accessible.
Summary In this lesson, you have learned the detailed process of acquiring Digital Forensics Evidence. You explored standard or proper ways for forensic investigators to acquire, handle, and analyze digital evidence. This unit provided critical standards and process applied by Digital Forensics Investigator in acquiring evidence, primarily using the Image Method in investigating financial frauds and Diagnosis of hardware networks. However, it worth to note that before acquiring the evidence, the investigator should first locate it. Digital evidence is typically found in hard drives, but with the current advancement in computing technology, evidence can be located in almost all digital-aware gadgets. The overall process of acquiring digital forensic evidence consists of different methods and requirements, which are critical for a digital forensic investigator.
References Akbal, E. & Dogan, S. (2018). Forensics Image Acquisition Process of Digital Evidence. International Journal of Computer Network and Information Security, 5: 1-8. DOI: 10.5815/ijcnis.2018.05.01 Ashcroft, J., Daniels, D. J. & Hart, S. V. (2019). Forensic Examination of Digital Evidence: A Guide for Law Enforcement. National Institute of Justice, Washington, DC. Retrieved from https://www.ncjrs.gov/pdffiles1/nij/199408.pdf Handigol, N., Heller, B., Jeyakumar,V,. Mazières,D. & McKeown, N. (2016). Where is the debugger for my software-defined network? In ACM SIGCOMM Workshop on Hot Topics in Software Defined Networking (HotSDN), 2(1): 895-915. Hassan, N. A. (2019). Digital forensics basics: A practical guide using windows OS. New York, NY: Springer Publishing. INFOSEC. (2019). Computer Forensics: Network Forensics Analysis and Examination Steps. Retrieved from https://resources.infosecinstitute.com/category/computerforensics/introduction/areasof-study/digital-forensics/network-forensics-analysis-and-examination-steps/#gref Kent, K., Chevalier, S., Grance, T. & Dang, H. (2006). Guide to Integrating Forensic Technique into Incident Response. NIST: Computer Security Resource Center. Retrieved from http://csrc.nist.gov/publications/nistpubs/800-86/SP800-86.pdf Nikkel, B. (2016). Practical forensic imaging: Securing digital evidence with Linux tools. San Francisco, CA: No Starch Press. Novak, M., Grier, J. & Gonzales, D. (2019). New Approaches to Digital Evidence Acquisition and Analysis. NIJ Journal, 280. Retrieved from https://www.ncjrs.gov/pdffiles1/nij/250700.pdf Prosise, C., & Mandia, K. (2003). Incident response & computer forensics. New York: McGraw-Hill Publishers. RSM. (2018). Fraud Investigations: How to uncover hidden financial accounts and assets. Retrieved from https://www.bizjournals.com/twincities/news/2018/11/20/fraud-investigationshow-to-uncover-hidden.html...
Similar Free PDFs

Digital Forensics Reports
- 4 Pages

Digital Forensics Intro
- 9 Pages

Digital Forensics Vocabulary
- 1 Pages

Documenting the Digital Evidence
- 5 Pages

- BN - Forensics
- 1 Pages

Acquisition and loss of territory
- 14 Pages

Merger and acquisition of flipkart
- 12 Pages

Law of Evidence Mcq
- 43 Pages

Evidence of evolution answers
- 8 Pages

Elements of Evidence Law
- 5 Pages
Popular Institutions
- Tinajero National High School - Annex
- Politeknik Caltex Riau
- Yokohama City University
- SGT University
- University of Al-Qadisiyah
- Divine Word College of Vigan
- Techniek College Rotterdam
- Universidade de Santiago
- Universiti Teknologi MARA Cawangan Johor Kampus Pasir Gudang
- Poltekkes Kemenkes Yogyakarta
- Baguio City National High School
- Colegio san marcos
- preparatoria uno
- Centro de Bachillerato Tecnológico Industrial y de Servicios No. 107
- Dalian Maritime University
- Quang Trung Secondary School
- Colegio Tecnológico en Informática
- Corporación Regional de Educación Superior
- Grupo CEDVA
- Dar Al Uloom University
- Centro de Estudios Preuniversitarios de la Universidad Nacional de Ingeniería
- 上智大学
- Aakash International School, Nuna Majara
- San Felipe Neri Catholic School
- Kang Chiao International School - New Taipei City
- Misamis Occidental National High School
- Institución Educativa Escuela Normal Juan Ladrilleros
- Kolehiyo ng Pantukan
- Batanes State College
- Instituto Continental
- Sekolah Menengah Kejuruan Kesehatan Kaltara (Tarakan)
- Colegio de La Inmaculada Concepcion - Cebu