Digital Forensics Intro PDF

| Title | Digital Forensics Intro |
|---|---|
| Author | Alan Cieślar |
| Course | Forensic IT |
| Institution | De Montfort University |
| Pages | 9 |
| File Size | 600.5 KB |
| File Type | |
| Total Downloads | 68 |
| Total Views | 137 |
Summary
Introduction into digital forensics and potential applications/cases...
Description
Digital Forensics Useful book to read – Guide to Computer Forensic Investigation; by Bill Nelson, Amelia Phillips, and Christopher Stuart; 4th Edition,;2010 Digital Forensics is “The use of scientifically proven methods to reconstruct past events that assist in criminal investigations by identifying relevant digital evidence.” (Carrier, 2003). – It involves obtaining and analysing digital information for use as evidence in civil, criminal, or discrimination cases – Nature of digital evidence is fragile – It is circumstantial, i.e. requires inference(s) to reach to a logical conclusion(s) – Digital Evidence includes hard disks/drives, mobile devices, CCTV etc. The principles of digital investigation No action (taken by digital investigators) should change data which may subsequently be relied upon in court In circumstances where a person finds it necessary to access original data, that person must be competent to do so and be able to give evidence explaining the relevance and the implications of their actions An audit trail or other record of all processes applied to digital evidence should be created and preserved. An independent third party should be able to examine those processes and achieve the same result The person in charge of the investigation has overall responsibility for ensuring that the law and these principles are adhered to Digital investigations and evidence The focus of a digital investigation is usually some type of digital device that has been involved in an incident or a crime. The digital device was either used to commit a physical crime: E.g. Suspect used the Internet to conduct research about a physical crime The digital device was tangential to the crime: Logs from smart fridge disproving suspect’s alibi
1
The digital device executed an event that violated a policy or law: Attacker gains unauthorized access to a computer User downloads contraband material User sends a threatening email or SMS
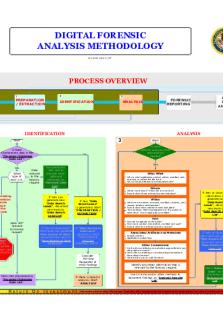
When a violation is detected, a digital investigation is started to answer questions such as why the violation occurred etc. Digital investigation is a process where we develop and test hypotheses that answer the questions about digital events This is done using a scientific method where we develop a hypothesis using the evidence that we find We then test the hypothesis by looking for additional evidence that shows the hypothesis is impossible Phases of Investigation Identification, Preservation, Analysis and Presentation Identification Identification is to locate the likely sources of evidence and seize them •
Look for any piece of equipment that can store evidence related to the crime being investigated
•
Collect peripheral hardware that may need examining by digital evidence examiner e.g., printers, scanners, etc.
•
Software: Installation disks
•
Removable media: Look for backups on-site or remote storage facilities. Keep in mind criminals often hide removable media containing incriminating information
•
Documentation related to hardware, software, and removable media
•
Passwords and important phone numbers on or near the computer. Passwords and other useful information may also be obtained through interviews with people involved
•
Trawl garbage for printouts and other evidence related to the computer
•
Photograph evidence in situ, paying attention to serial numbers and wiring to help identify equipment and aid reconstruction. Vivid documentation showing evidence in its original state can be useful for reconstruction of a crime and demonstrating that evidence is authentic. 2
•
Consider removing casing and photographing internal components including closeups of jumper settings and other details
•
Note or photograph the contents of the computer screen.
•
If a program is running that might be destroying data, immediately disconnect power by pulling the cable
•
If a system is on, a judgement must be made as to whether to gather information from the system. Use trusted utilities such as statically compiled executables on a CDROM. Any actions performed on the system must be clearly documented to enable others assess the impact this process had on the system
Preservation Preservation is to preserve the state of the digital crime scene. •
Actions that are taken in this phase vary depending on the legal, business, or operational requirements,
•
The purpose is to reduce the amount of evidence that may be overwritten,
•
This process continues after data acquisition from the system because we need to preserve data for future analysis,
•
Since the goal of this phase is to reduce the amount of evidence that is overwritten, we want to limit the number of processes that can write to the storage devices,
•
For a static acquisition we will terminate all processes by turning the system off and make duplicate copies of all the data.
•
Write blockers can prevent evidence from being overwritten
•
For a live acquisition important data should be copied from the system in case it is overwritten while searching for evidence
•
For example, if you are going to be reading files, then you can save the temporal data for each file so that you have a copy of the last access times before you cause them to be updated
•
When important data are saved during a static or live acquisition, a cryptographic hash (MD5, SHA-1, and SHA-256) should be calculated to later show that the data have not been changed
General preservation guidelines: •
Duplication: Copy important data, put the original in a safe place, and analyze the copy so that you can restore the original if the data is modified, 3
•
Calculate MD5 or SHA hashes of important data so that you can later prove that the data has not been changed,
•
Use a write-blocking device during procedures that could write to the suspect data. Minimize the number of files created during a live analysis because they could overwrite evidence in unallocated space,
•
Be careful when opening files on the suspect system during a live analysis because you could be modifying data, such as the last access time.
•
Label, date, initial all evidence
•
Where possible, copy of digital evidence should be preserved on WORM (Write once read many) storage media suitable for long term storage such as CD
•
Store in sealed envelopes and secure in an evidence room or safe
•
Ensure that the chain of custody is maintained throughout
Chain of custody- answer to the following questions: •
Where, when, how, and by whom was the evidence discovered and collected?
•
Where, when, and by whom was the evidence handled or examined?
•
Who had custody of the evidence, during what period. How was it stored?
•
When the evidence changed custody, when, and how did the transfer occur (include shipping numbers, etc.).
Analysis According to EC-council there are four ways a digital forensics investigator can analyse the evidence: •
Time frame analysis: Determines what file activity occurred on the computer during a particular time and examines various system log files to correlate file system activities with other activities,
•
Data-hiding analysis: Looks for ways that information may be hidden either within the file system or in portion of the disk that are normally inaccessible to standard file system access,
•
Application and file analysis: Look at the contents of files, map files to applications, and maps application activity to file creation and deletion -> e.g., mapping email messages to file attachments.
4
•
Ownership and possession analysis: Can help identify activities tied to a particular login account, such as file deletion, modification, or attempts to change the owner of a particular file
Note: These activities are not mutually exclusive. Each type of analysis will probably be performed during an investigation Physical vs. Logical analysis •
Physical analysis looks at actual disk blocks,
•
Physical analysis can produce information that is not accessible via logical analysis,
•
You can perform keyword searches across physical disk blocks,
•
Extract files from disk using a technique called ‘file carving’,
•
Retrieve free space on the disk
•
Logical analysis examines the data via the file system that has been created on the disk,
•
Logical analysis is useful for retrieving information like filenames and sizes, file types, and other metadata stored concerning the state of the file system (file slack space, unallocated space, etc.)
Presentation Once analysis is completed you will need to write a report •
The final investigative report will be a complete report that is based on all the evidence that has been collected and analysed.
•
You will base your final report on the documentation that you created at each step of the process,
•
Make sure to document each step in your analysis and results, time and date stamping each entry in your log. An entry might look like the following:
27/7/2016 3:00 PM BST. Performed a keyword search on the contents of USB drive ZZZ. Discovered the name of a primary client of QQQ company. Further investigation discovered that the name was in a deleted file labelled thoughts.txt. Contents of the file appear to be a letter to the head of sales of QQQ, introducing the suspect and making an offer to the head of sales concerning supplying contract details for other clients of company QQQ. Analysis of the mail log files indicated that this file was included as an attachment e-mailed to the head of sales five minutes prior to file deletion.
5
Your report must provide a systematic, thorough, and unbiased presentation of your findings.
The structure must be clear and logical Content: Should relate to the issues in the case, Provide evidence of the facts, State the source of the evidence,
The report must be understood by the court. Know your audience. Preparing the scene
Review facts, plans, and objectives with the investigation team you have assembled Slow response can cause digital evidence to be lost Goals Preserve the evidence Keep information confidential Define a secure perimeter Use barrier tape Legal authority Professional curiosity can destroy evidence Involves police officers and other professionals who are not part of the crime scene processing team – Keep them out/controlled
Evidence you acquire depends on the case - Ask: •
Do you need the entire computer and all peripherals and media in the immediate area?
•
How are you protecting the evidence transporting them to your lab?
•
Is the computer powered on when you arrive?
•
Is the suspect you are investigating in the immediate area of the computer?
•
Is it possible the suspect damaged or destroyed anything?
•
Will you have to separate the suspect from the computer?
6
7
8
Summary – In Digital Investigation the process is key. – Four phases: Identification, preservation, analysis, reporting. – All sources of potential evidence should be identified and processed accordingly. – Preserve evidence by making forensic duplicates and working from the duplicates. – The final report must be understandable by your target audience.
9...
Similar Free PDFs

Digital Forensics Intro
- 9 Pages

Digital Forensics Reports
- 4 Pages

Digital Forensics Vocabulary
- 1 Pages

- BN - Forensics
- 1 Pages

Forensics Crash Course
- 1 Pages

Forensics Chapter 1
- 5 Pages

Forensics Welcome Intrusion
- 1 Pages

Forensics on Trail Video
- 2 Pages

Chapter 1-11 forensics
- 39 Pages
Popular Institutions
- Tinajero National High School - Annex
- Politeknik Caltex Riau
- Yokohama City University
- SGT University
- University of Al-Qadisiyah
- Divine Word College of Vigan
- Techniek College Rotterdam
- Universidade de Santiago
- Universiti Teknologi MARA Cawangan Johor Kampus Pasir Gudang
- Poltekkes Kemenkes Yogyakarta
- Baguio City National High School
- Colegio san marcos
- preparatoria uno
- Centro de Bachillerato Tecnológico Industrial y de Servicios No. 107
- Dalian Maritime University
- Quang Trung Secondary School
- Colegio Tecnológico en Informática
- Corporación Regional de Educación Superior
- Grupo CEDVA
- Dar Al Uloom University
- Centro de Estudios Preuniversitarios de la Universidad Nacional de Ingeniería
- 上智大学
- Aakash International School, Nuna Majara
- San Felipe Neri Catholic School
- Kang Chiao International School - New Taipei City
- Misamis Occidental National High School
- Institución Educativa Escuela Normal Juan Ladrilleros
- Kolehiyo ng Pantukan
- Batanes State College
- Instituto Continental
- Sekolah Menengah Kejuruan Kesehatan Kaltara (Tarakan)
- Colegio de La Inmaculada Concepcion - Cebu