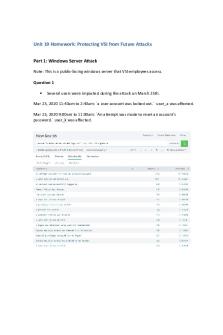
Assignment - 1 mahi - worm attacks PDF

| Title | Assignment - 1 mahi - worm attacks |
|---|---|
| Author | Tejus Ahuja |
| Course | International Business |
| Institution | Edith Cowan University |
| Pages | 11 |
| File Size | 474.1 KB |
| File Type | |
| Total Downloads | 5 |
| Total Views | 145 |
Summary
worm attacks...
Description
CSI1101D
COMPUTER SECURITY
ASSIGNMENT-1
Table of Contents Section 1: Worm Internet Attack.................................................................................................................2 Process of Worm spread..............................................................................................................................3 System targeted by the worm………………………………………………………………………………………………………………….6 Worm Structure………………………………………………………………………………………………………………………………………6 Worm attack................................................................................................................................................7 Worm defense…………………………………………………………………………………………………………………………………………7 Worm User………………………………………………………………………………………………………………………………………………7 Section 2: A Case Study...............................................................................................................................8 Morris Internet Worm.................................................................................................................................8 Morris worm founder..................................................................................................................................9 Impact.........................................................................................................................................................9 Court decisions............................................................................................................................................ 9 1|Page
CSI1101D
COMPUTER SECURITY
ASSIGNMENT-1
Summary................................................................................................................................................... 10 References.................................................................................................................................................11
Section 1: Worm Internet Attack. Unlike Trojans and Viruses which spread following human intervention, worm(s) is software that replicates itself and is programmed such that it can move on its own throughout a network, Figure 1 (Moore & Claffy, n.d.).
2|Page
CSI1101D
COMPUTER SECURITY
ASSIGNMENT-1
Fig 1 a
Figure 1b: Process of Worm spread
Process of Worm spread Tang, Luo, Xiao and Wei, (2009) states that, worms use infected hosts to cause other forms of attacks, slow the network, remove files, steal sensitive information and compromise systems,
3|Page
CSI1101D
COMPUTER SECURITY
ASSIGNMENT-1
Fig 2a and b. Today Worm pose a great problem to computer internet functionability. Currently, there are worms that may appear as IM (instant messaging) and P2P worm, the worm moves faster is compared to the human ability to delete the worms manually and, with adaptation of metamorphism and polymorphism techniques worms are cautious Fig 2c.
Fig 2a The Worm point of Local Area Network targets
Fig 2b: The Worm point of Local Area Network targets
4|Page
CSI1101D
COMPUTER SECURITY
ASSIGNMENT-1
Fig 2c: Systems targeted by the worm complicating human rate of defense According to Pratama and Rafrastara, (2012) the attackers use the computer worm for many reasons: one to increase the damage, two to make trackback hard and reach as many systems as possible. The computer worm can be bad to the computer systems as it takes control of large computer networks and by using it they destroy the network, Fig 1 and Figure 2b. The ten most destructive computer worms are: CIH, Blaster, Sasser, SQL Slammer, Melissa Virus, Code Red, Conficker, ILOVEYOU, Sobiq.F and MyDoom. The computer worms are classified into four main classes: how the user fight the worm, how the worm defends itself from being detected, how the worm attacks and on its structure, sees figures 3, a, b, c and d below.
Figure 3a: Worm structure A computer worm has some fundamental parts with each part designed to carry out a certain function: self-tracking, payload, life-cycle manager, remote control and update interface and infection propagation.
5|Page
CSI1101D
COMPUTER SECURITY
ASSIGNMENT-1
Fig 3a: Worm Structure
Worm attack Worm attack classification gives an insight on the strategy used by a worm to attack the vulnerable computer system, figure 3b: Worm attack
Fig 3b: Worm Attack
6|Page
CSI1101D
COMPUTER SECURITY
ASSIGNMENT-1
The computer worm uses various ways to avoid being detected see, Figure 3
Figure 3c: Worm Defense Figure 3d, brings out various ways that a user might employ to prevent the threat of worm invasion and penetration.
Figure 3d: User Defense
7|Page
CSI1101D
COMPUTER SECURITY
ASSIGNMENT-1
Section 2: A Case Study
Morris Internet Worm According to Moore and Claffy, (n.d.) in 1988/11/2 at 18:00 a 99-line-program was released into the internet by Robert T. Morris. Andy Sudduth of Havard University on 1988/11/3 at 00:34 posted a message stating that, “There is probably a virus loosely affecting the internet, (Moore & Claffy, (n.d.), p273)”. The Morris worm did attack thousands of VAX computers and UNIX operated Sun workstations which were attached to the Research Internet critically; interfering with service provision for some days an act which was well known by an insider. The act also brought into limelight a number of security weaknesses (Denning, 1989). Morris worm affected majorly an open network with a little information on the impact this worm brought to the closed network (Denning, 1989). During this time, in Sun and VAX, machines all over the country were screaming and subsequently would stop as unseen tasks used all resources available. Previously, although viruses were being reported, none had ever caused such a large number of computers within the nation to stop functioning, rather Morris worm was the first ever in history of computers to cause serious damage because other earlier worms were designed to make maximum use of networked computation resources (Moore & Claffy, n.d.). Denning (1989) invaded computers were overwhelmed by the huge programs load that appeared like harmless “shell”: programs (command interpreters). Expertise tried to stop and kill the worms in vain as more new copies were being reproduced from the internet connections on deleting the old copies. Most systems were shut down and all suspicious security opening closed before re-starting the network with no re-infection. UNIX experts, unexpectedly opened the annual meeting at Berkeley on 1988/11/3 morning. They worked to dissect and capture the worm as fast as they could to stop the damage. On the evening of the same day, the UNIX expertise had distributed system to fix the problem to almost all the security loopholes the Morris worm used to infest new systems. MIT team amongst other institutions, at Berkely, on 1988/11/4 morning, decompiled the code of the worm and examined its structure using programming language C. The expertise confirmed that the worm neither deleted nor modified files present in a computer during the attack. The worm did not transmit passwords, exploit superuser privileges or install Trojan horses decoded. The worm was only spread via the TCP/IP network protocols and infected specifically Berkely UNIX
8|Page
CSI1101D
COMPUTER SECURITY
ASSIGNMENT-1
computers but, not AT&T System V UNIX. This brought a breathtaking moment amongst most users as administrators installed the fixes, removed all copies of the worm and started again all the downed systems (Jajoo, 2018). By 1988/11/6 most hosts had been relinked to the Internet although the worm would delay a little longer up to 1988/11/10 before disconnecting while mail backlogs remained until 1988/11/12. The damage was massive affecting almost 3,000-4000 computers a 5% of Internetworked computers (Dennings, 1989).
Morris worm founder A computer worm was launched on 1988/11/2 around 6 pm by a Cornell university gradstudent; then a first year, Robert Tappan Morris. From Morris point of view, the worm which later interfered with the whole Internet system was only for educational purposes (Jajoo, 2018). The self-propagating and self-replicating worm was produced by Morris and released from an MIT, but not Cornell University. The worm was authored such that it appeared to have come from Berkeley, (Boettger, 2000).
Impact The Morris internet worm was found to cause massive destruction. First the financial goals were impacted in the sense that, there was loss of internet for a period of time a loss estimated at $100,000-10,000,000, Time/ and labour time goals were also affected as the recovery period involved massive human power and schedule/ and production goals effects was that there was a delay in internet access (ThinkReliability, 2003).
Court decisions Morris act, then a first year computer science student at the Cornell University was found to be unlawful and unethical as he was termed to have ignored the well-known potential consequence of his act. The commission investigating his case reported that Morris act was probably that of a hacker who was thoughtfully absorbed in his action of creating, knowing well the potential effect or with a clear purpose (Eisenberg, Gries, Hartmanis, Holcomb, Lynn and Santoro, 1989). A federal Jury would later on 1/23/1990 convict a 24-year-old Robert Tappan Morris, a computer student to a 3-year suspended jail sentence, a fine of up to $250,000 and a community service of 400 hours as his sole intention was to break into as many computer systems in the US as possible, (Markoff, 1990).
9|Page
CSI1101D
COMPUTER SECURITY
ASSIGNMENT-1
Summary Worm is a program that attacks a computer internet, spreading to the whole of computer system and attacking local area networks sometimes causing massive damage. Morris worm was invented by Robert T Morris with sole intention of invading as many computers as possible. On 1988/11/2 at 18:00 a 99-line-program was released into the internet by Robert T. Morris. The worm did replicate itself even after being deleted. The system would in turn be overloaded at long last coming to a standstill. The Morris worm affected about 2000-4000 computers, a problem which was costly and involved human power effort to rectify. On 1/23/1990 Morris was convicted; a suspended jail sentence, a fine of up to $250,000 and a community service of 400 hours
10 | P a g e
CSI1101D
COMPUTER SECURITY
ASSIGNMENT-1
References Boettger, L. (2000). The Morris Worm: How it Affected Computer Security and Lessons Learned By It. SANS Institute. Denning, P.J. (1989). Internet Worm. RIACs Technical Report TR-89.3. Research Institute for Advanced Computer Science NASA Ames Research Center. Eisenberg, T., Gries, D., Hartmanis, J., Holcomb, D., Lynn, M.S. and Santoro, T. (1989). The Cornell Commission: On Morris and the Worm. Communication of the ACM, 32(6):706-710. Jajoo, A. (2018). A Study on the Morris Worm. Purdue University. Markoff, J. (1990). Computer Intruder is Found Guilty. The New York Times, Retrieved from, https://www.nytimes.com/1990/01/23/us/computer-intruder-is-found-guilty.html Moore, D. and Clafffy, C.S. (n.d.). Code-Red: A Case Study on the Spread and Victims of an Internet Worm. Retrieved from, https://www.eecis.udel.edu/~mills/teaching/eleg867b/dos/p273moore.pdf. Pratama, A. and Rafrastara, F.A. (2012). Computer worm classification. International Journal of Computer Science and Information Security, 10(4):21-24. Tang, Y., Luo, J., Xiao, B. and Wei, G. (2009). Concept, characteristics and defending mechanism of worms. IEICE Trans Inf and Syst, 92(5):799-810. ThinkReliability, (2013). The Morris Worm: The First Significant Cyber Attack. Retrieved from, https://www.thinkreliability.com/InstructorBlogs/blog-MorrisWorm.pdf
11 | P a g e...
Similar Free PDFs

Assignment - 1 mahi - worm attacks
- 11 Pages

Lab 1 TCP IP Attacks
- 15 Pages

Assignment 1
- 10 Pages

Assignment 1
- 3 Pages

Assignment 1
- 3 Pages

Assignment 1
- 9 Pages

Assignment 1
- 10 Pages

Assignment 1
- 2 Pages

Assignment 1
- 6 Pages

Assignment 1
- 16 Pages
Popular Institutions
- Tinajero National High School - Annex
- Politeknik Caltex Riau
- Yokohama City University
- SGT University
- University of Al-Qadisiyah
- Divine Word College of Vigan
- Techniek College Rotterdam
- Universidade de Santiago
- Universiti Teknologi MARA Cawangan Johor Kampus Pasir Gudang
- Poltekkes Kemenkes Yogyakarta
- Baguio City National High School
- Colegio san marcos
- preparatoria uno
- Centro de Bachillerato Tecnológico Industrial y de Servicios No. 107
- Dalian Maritime University
- Quang Trung Secondary School
- Colegio Tecnológico en Informática
- Corporación Regional de Educación Superior
- Grupo CEDVA
- Dar Al Uloom University
- Centro de Estudios Preuniversitarios de la Universidad Nacional de Ingeniería
- 上智大学
- Aakash International School, Nuna Majara
- San Felipe Neri Catholic School
- Kang Chiao International School - New Taipei City
- Misamis Occidental National High School
- Institución Educativa Escuela Normal Juan Ladrilleros
- Kolehiyo ng Pantukan
- Batanes State College
- Instituto Continental
- Sekolah Menengah Kejuruan Kesehatan Kaltara (Tarakan)
- Colegio de La Inmaculada Concepcion - Cebu